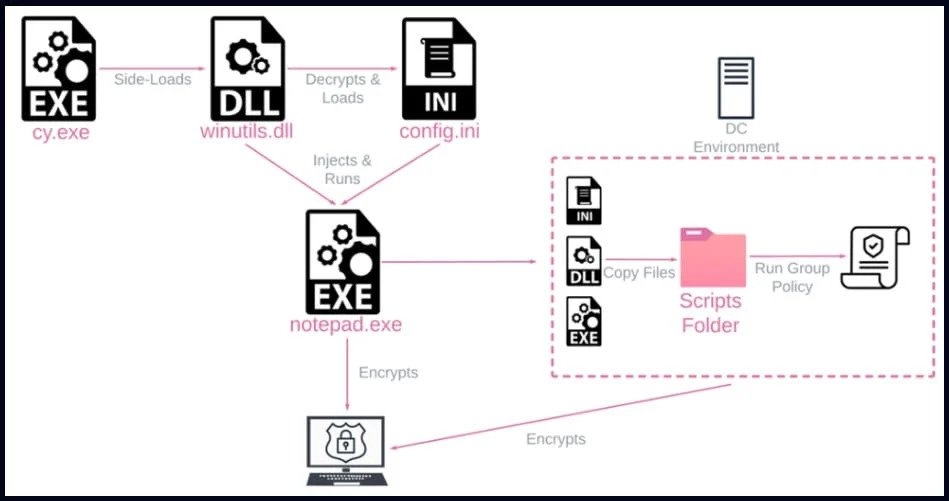
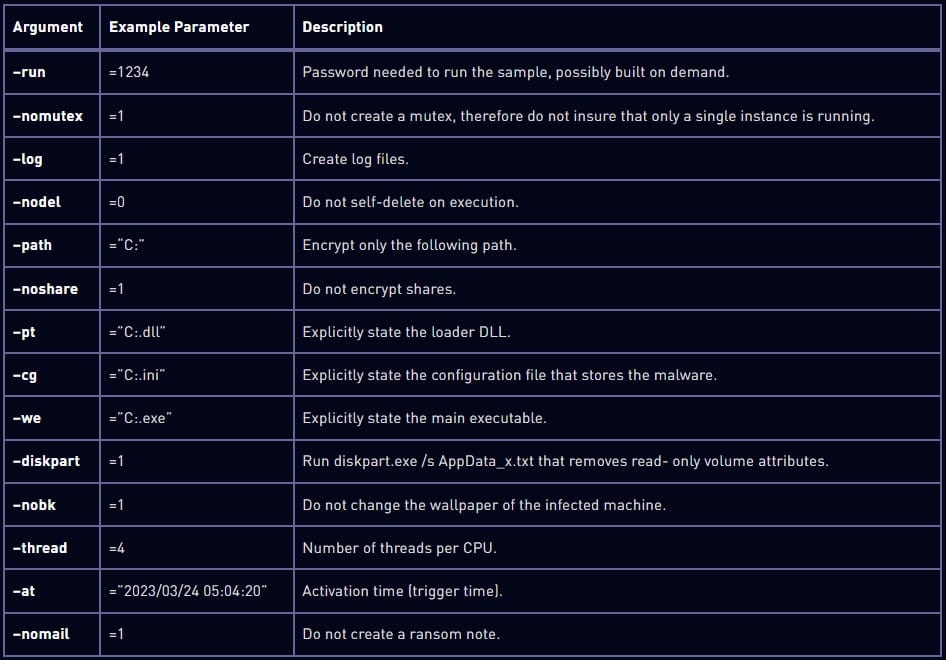
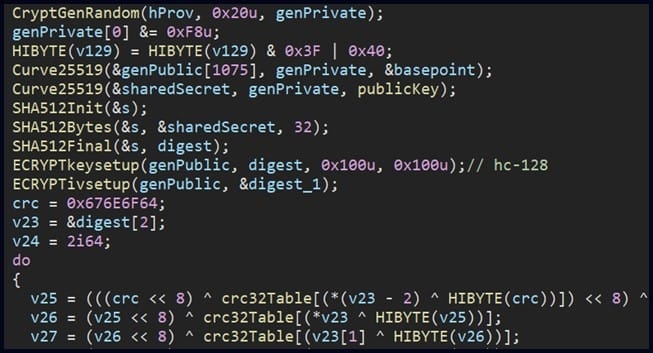
This report comes after the security firm analyzed a cyberattack on a US-based firm. In its report, Security firm Check Point mentions that the attacker deployed malware on the victim’s network after taking advantage of a flaw in the victim’s threat detection & incident response tool. Also, Rorschach was distributed using a DLL side loading method via a signed part in Cortex XDR, A extended detection & response product from Palo Alto Network. The attackers used the Cortex XDR Dump Service tool (cy.exe) 7.3.0.1.6740 version to sideload the Rorschach loader & injector (winutils.dll), which then leads to the payload “config.ini” into a Notepad process. The files with the loader have UPX anti-analysis protection, while the main payload is protected from reserve engineering and detection by virtualizing parts of the code using the VM Protect software. Check Point says the ransomware Rorschach creates a Group Policy when carried out on a Windows Domain Controller spread to other hosts on the domain. As the machine gets infected, the malware then deletes the four event logs, i.e., Security, System, Application, and the Window Powershell, to erase any existence of it. Read: Attackers Sending IRS Phishing Emails to Install Emotett Malware With that being said, although the malware comes with a hard-coded configuration, it supports command-line arguments that increase functionality. Well, the options are hidden and are not accessible without reverse engineering the malware, says Check Point. Rorschach will begin the encryption data only if the victim machine is configured with a language outside of the Commonwealth of Independent States. The encryption scheme mixes the curve25519 & eSTREAM cipher hc-128 algorithm and follows the occasional encryption trend; for instance, it only encrypts the file partially, lending to increase processing speed. Check Point says following the basic routine of the malware reveals a highly successful execution of thread scheduling via I/O completion ports. “In addition, it appears that compiler optimization is prioritized for speed, with much of the code being inclined. All of these factors make us believe that we may be dealing with one of the fastest ransomware out there”, mentions Check Point. The security firm ran a test to find how fast Rorschach encryption is, a test which had 220,000 files set up on a Six core CPU PC, and it took Rorschach about 4.5 minutes to encrypt all data and in the meantime LockBit v3.0, which is considered the fastest ransomware strain finished in about 7 minutes. As the malware locks the system, it sends out a ransom note identical to the format used by the Yanglowang ransomware. Now according to researchers, a previous malware also used a similar ransomware note as DrkSide. This similarity is likely what caused researchers to mistake a different version of Rorschach with DarkSide, an activity that was revamped to Black Matter in 2021 and then vanished the same year. Check Point says that Rorschach has made some better features from some of the best ransomware that leaked online, i.e., LockBit v2.0, DarkSide & more. At the moment, the security firm says Rorschach’s activities are not known, and moreover, there’s no branding of it, which is rarely seen in the ransomware side of things. Read: Common Magic & Power Magic Malware Used in Advanced Surveillance Attacks